External Authentication Providers
Multiple external authentication providers can be defined using [provider.x] sections:
[provider.1]
type = oidc
# Provider type, currently only oidc is available
name = OIDC Example
# Display name
issuer = example
# issuer of the tokens. Can be "google", "microsoft"
# or an arbitrary string for custom identity
# providers
icon = url('data:image/svg+xml;base64,...')
# Optional display icon. Can be either a remote or
# a data URL. If omitted, a default icon is used
# based on type and provider.
metadata_url = https://example.com/auth/realms/<realm>
# URL to get OIDC metadata from. Can be obtained
# from the provider.
# It usually contains a realm or tenant id.
client_id = <client-id>
# OIDC client secret. Can be obtained from the
# provider. Some providers call this "app id".
client_secret = <client-secret->
# OIDC client secret. Can be obtained from the
# provider. Some providers call this "secret value".
hidden = false
# it is possible to hide an authentication provider
# on the SKOOR Auth start page. This can be useful
# if e.g. normal users authenticate against a public
# provider and support employees against an internal
# one.
Microsoft Azure AD OpenID Connect
SKOOR Auth Provider Entry
[provider.1] type = oidc name = Azure AD Example issuer = microsoft metadata_url = https://login.microsoftonline.com/<tenant-id>/v2.0 client_id = <app-id> client_secret = <secret-value>
The icon is set automatically based on the issuer name.
Required Settings in Azure AD
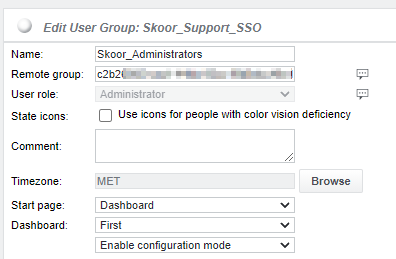
Azure group ID to match SKOOR remote group:
In order to allow users to login and get the correct Role assigned these ID’s must be configured.
In the example below, all Users in the Azure AD Group with the ID c2b2***** will have the administrator role after login:
App registration
In your Azure Active Directory you register a new application, choose supported account types based on your AD Setup (Single- or Multi- tenant).
As Redirect URI configure the following, depending on which services your server has activated. This can also be edited later on.
Skoor Engine / Skoor Dashboard | https://<FQDN>/skoor-auth/oidc/code |
Skoor Dashboard Viewer | https://FQDN/skoor-dashboard-viewer-auth/oidc/code |
Tenant ID & Client ID
Once the application registration is saved, open the overview tab of the created application and take note of the two ID’s which will later be required for the configuration. These are called:
Application (client) ID
Directory (tenant) ID
Certificates & secrets
Next, go to Certificates & secrets and add a client secret. Set a name for this secret and pick an expiration date. Once saved you can see the secret id and the secret value. The secret value is later required to configure the Skoor Auth service.
Token
Go to the token configuration and select ‘add groups claim'. In the claim configuration select ‘Security groups’ and select the token property Type ‘ID’ to ‘sAMAccountName’.
API Permission
This step is optional. To enable more details on the user configuration in Skoor, for example the profile picture, the application needs permission to read the full user profile.
Therefor you can perform the following steps in the tab ‘API permissions’:
Add permission
Select Microsoft Graph
Delegated Permissions
Search for User.Read or scroll the section ‘user’ and select ‘User.Read’ then click ‘add permission’
Back in the overview confirm the permission by selecting ‘Grant admin consent’
Keycloak
SKOOR Auth Provider Entry
[provider.2]
type = oidc
name = SKOOR Keycloak
issuer = skoor
icon = url('data:image/svg+xml;base64,PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiIHN0YW5kYWxvbmU9Im5vIj8+CjxzdmcKICAgeG1sbnM6ZGM9Imh0dHA6Ly9wdXJsLm9yZy9kYy9lbGVtZW50cy8xLjEvIgogICB4bWxuczpjYz0iaHR0cDovL2NyZWF0aXZlY29tbW9ucy5vcmcvbnMjIgogICB4bWxuczpyZGY9Imh0dHA6Ly93d3cudzMub3JnLzE5OTkvMDIvMjItcmRmLXN5bnRheC1ucyMiCiAgIHhtbG5zOnN2Zz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciCiAgIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8yMDAwL3N2ZyIKICAgeG1sbnM6c29kaXBvZGk9Imh0dHA6Ly9zb2RpcG9kaS5zb3VyY2Vmb3JnZS5uZXQvRFREL3NvZGlwb2RpLTAuZHRkIgogICB4bWxuczppbmtzY2FwZT0iaHR0cDovL3d3dy5pbmtzY2FwZS5vcmcvbmFtZXNwYWNlcy9pbmtzY2FwZSIKICAgdmlld0JveD0iMCAwIDI1LjAwMDAwMSAyNSIKICAgaGVpZ2h0PSIyNSIKICAgd2lkdGg9IjI1IgogICB4bWw6c3BhY2U9InByZXNlcnZlIgogICBpZD0ic3ZnMiIKICAgdmVyc2lvbj0iMS4xIgogICBzb2RpcG9kaTpkb2NuYW1lPSJza29vci1jaXJjbGUuc3ZnIgogICBpbmtzY2FwZTp2ZXJzaW9uPSIwLjkyLjUgKDIwNjBlYzFmOWYsIDIwMjAtMDQtMDgpIj48c29kaXBvZGk6bmFtZWR2aWV3CiAgICAgcGFnZWNvbG9yPSIjZmZmZmZmIgogICAgIGJvcmRlcmNvbG9yPSIjNjY2NjY2IgogICAgIGJvcmRlcm9wYWNpdHk9IjEiCiAgICAgb2JqZWN0dG9sZXJhbmNlPSIxMCIKICAgICBncmlkdG9sZXJhbmNlPSIxMCIKICAgICBndWlkZXRvbGVyYW5jZT0iMTAiCiAgICAgaW5rc2NhcGU6cGFnZW9wYWNpdHk9IjAiCiAgICAgaW5rc2NhcGU6cGFnZXNoYWRvdz0iMiIKICAgICBpbmtzY2FwZTp3aW5kb3ctd2lkdGg9IjE5MjAiCiAgICAgaW5rc2NhcGU6d2luZG93LWhlaWdodD0iMTAxNiIKICAgICBpZD0ibmFtZWR2aWV3MTMiCiAgICAgc2hvd2dyaWQ9ImZhbHNlIgogICAgIGlua3NjYXBlOnpvb209IjIyLjIyNjk2NyIKICAgICBpbmtzY2FwZTpjeD0iOC4yODU2MDM4IgogICAgIGlua3NjYXBlOmN5PSIxMy42MjkyMjYiCiAgICAgaW5rc2NhcGU6d2luZG93LXg9IjAiCiAgICAgaW5rc2NhcGU6d2luZG93LXk9IjI3IgogICAgIGlua3NjYXBlOndpbmRvdy1tYXhpbWl6ZWQ9IjEiCiAgICAgaW5rc2NhcGU6Y3VycmVudC1sYXllcj0ic3ZnMiIKICAgICBmaXQtbWFyZ2luLXRvcD0iMCIKICAgICBmaXQtbWFyZ2luLWxlZnQ9IjAiCiAgICAgZml0LW1hcmdpbi1yaWdodD0iMCIKICAgICBmaXQtbWFyZ2luLWJvdHRvbT0iMCIgLz48bWV0YWRhdGEKICAgICBpZD0ibWV0YWRhdGE4Ij48cmRmOlJERj48Y2M6V29yawogICAgICAgICByZGY6YWJvdXQ9IiI+PGRjOmZvcm1hdD5pbWFnZS9zdmcreG1sPC9kYzpmb3JtYXQ+PGRjOnR5cGUKICAgICAgICAgICByZGY6cmVzb3VyY2U9Imh0dHA6Ly9wdXJsLm9yZy9kYy9kY21pdHlwZS9TdGlsbEltYWdlIiAvPjxkYzp0aXRsZT48L2RjOnRpdGxlPjwvY2M6V29yaz48L3JkZjpSREY+PC9tZXRhZGF0YT48ZGVmcwogICAgIGlkPSJkZWZzNiIgLz48cGF0aAogICAgIGlkPSJwYXRoMjQiCiAgICAgc3R5bGU9ImZpbGw6I2UyMDA3YTtmaWxsLW9wYWNpdHk6MTtmaWxsLXJ1bGU6bm9uemVybztzdHJva2U6bm9uZTtzdHJva2Utd2lkdGg6MC4wMjg2ODc3NSIKICAgICBkPSJtIDYuMDkzODUyMiwxMi4xNzc1MjUgYyAwLDMuODgzNDYgMi44Njc5MTM1LDYuNzIwOTY2IDYuMzYyMzY2OCw2LjcyMDk2NiAzLjQ5NTAyOSwwIDYuMzYyOTQ1LC0yLjgzNzUwNiA2LjM2Mjk0NSwtNi43MjA5NjYgMCwtMy4xMDYyOTU2IC0yLjg2NzkxNiwtNS45NDM4MDA1IC02LjM2Mjk0NSwtNS45NDM4MDA1IC0zLjQ5NDQ1MzMsMCAtNi4zNjIzNjY4LDIuODM3NTA0OSAtNi4zNjIzNjY4LDUuOTQzODAwNSB6IE0gMjQuOTEyNDQxLDEyLjE0Nzk4IGMgMCw3LjI4ODY5NiAtNS4yMjcxOTUsMTIuNDI2NjcyIC0xMi40NTYyMjIsMTIuNDI2NjcyIEMgNS4yMjc0ODE1LDI0LjU3NDY0OSAwLDE5LjQzNjY3MiAwLDEyLjE0Nzk3NyAwLDUuMzM3NTE5MyA1Ljk3NDIyNDMsMC41NTc4NTM0NSAxMi40NTYyMTksMC41NTc4NTM0NSBjIDYuNDgyMjg0LDAgMTIuNDU2MjIyLDQuNzc5NjY1ODUgMTIuNDU2MjIyLDExLjU5MDEyMzU1IgogICAgIGlua3NjYXBlOmNvbm5lY3Rvci1jdXJ2YXR1cmU9IjAiIC8+PC9zdmc+')
metadata_url = https://<keycloak-server-address>/auth/realms/<realm>
client_id = <client-id>
client_secret = <client-secret>
Since we have a custom issuer, we have to provide an icon to display next to the name. We can provide the icon using a data URL.
Required Settings in Keycloak
The following is a minimum configuration to get a OIDC with Keycloak working. This can be used if you don’t already have an OIDC compatible authentication provider and want to authenticate your users against an internal active directory.
Realm Settings
If you don’t already have a realm configured, you have do add one. A good realm name might be your company name. This name is the value you need to insert as <realm> in your provider entry.
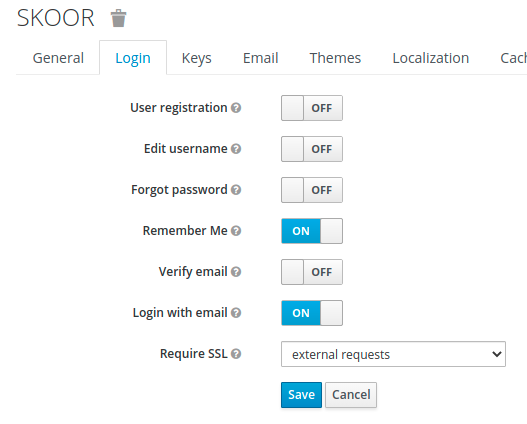
It might be a good idea to enable Remember Me option on the Login tab.
Clients
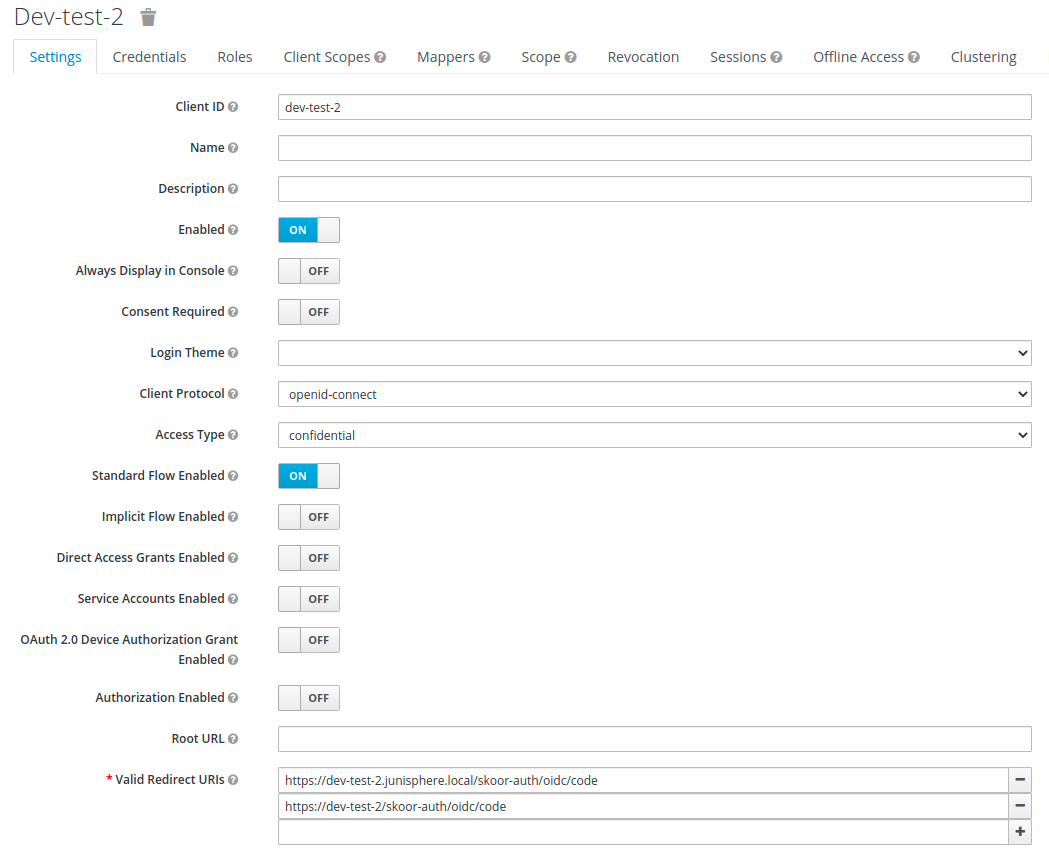
You have to add a client configuration for SKOOR.
Client ID has to be inserted as <client_id> in you provider config.
Client protocol has to be openid-connect.
Access Type has to be confidential
Standard flow has to be enabled.
Redirect URLs should be set to the following values:
Skoor Engine / Skoor Dashboards | https://<FQDN>/skoor-auth/oidc/code |
Skoor Dashboard Viewer |
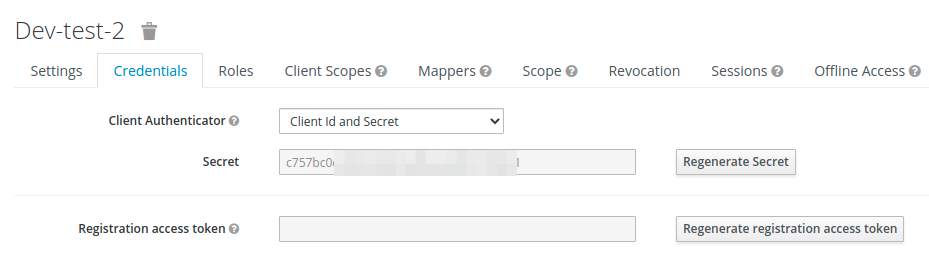
The client secret needed for the <client_secret> provider config you can get from the Credentials tab.
Client Scopes
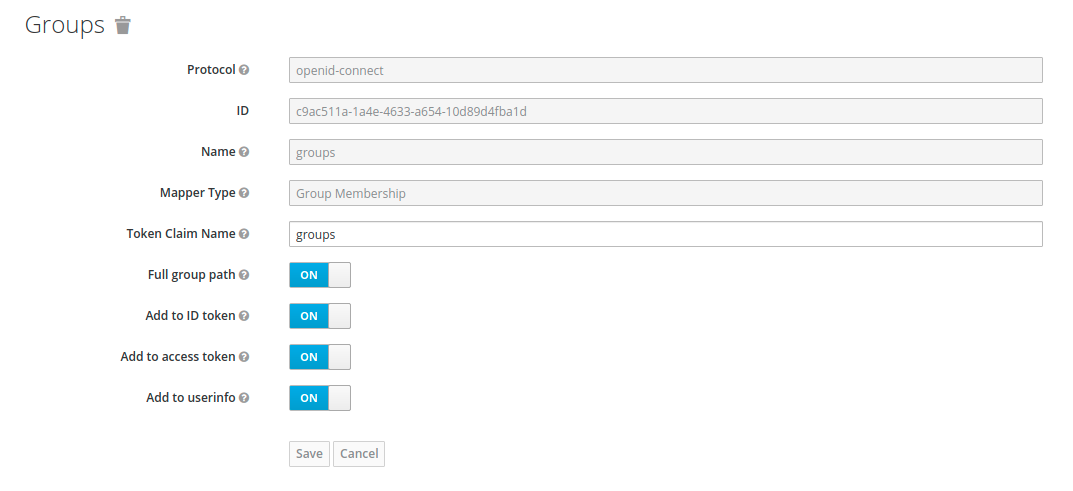
In order to get group information for a user, an additional mapper called groups has to be added to the profile scope.
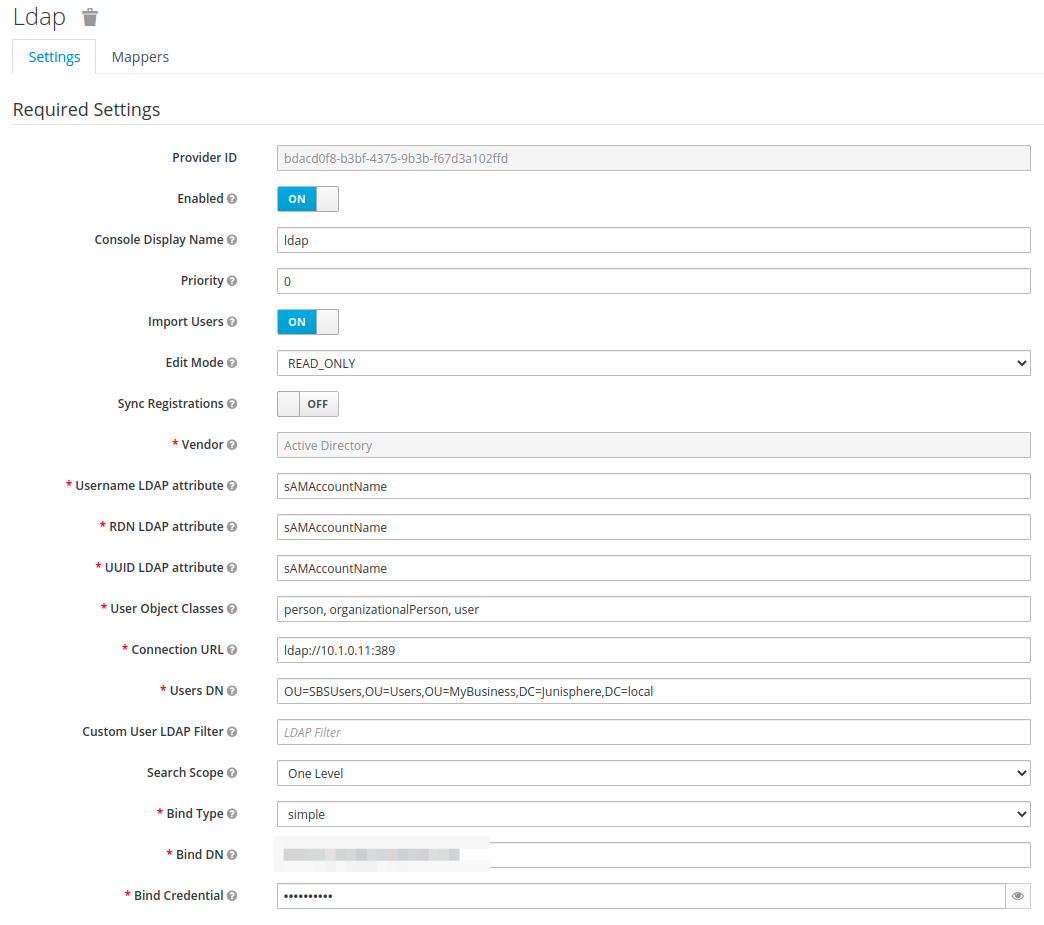
User Federation
In order to be able to authenticate against a active directory, a LDAP provider has to be added.
This settings heavily depends on your AD configuration
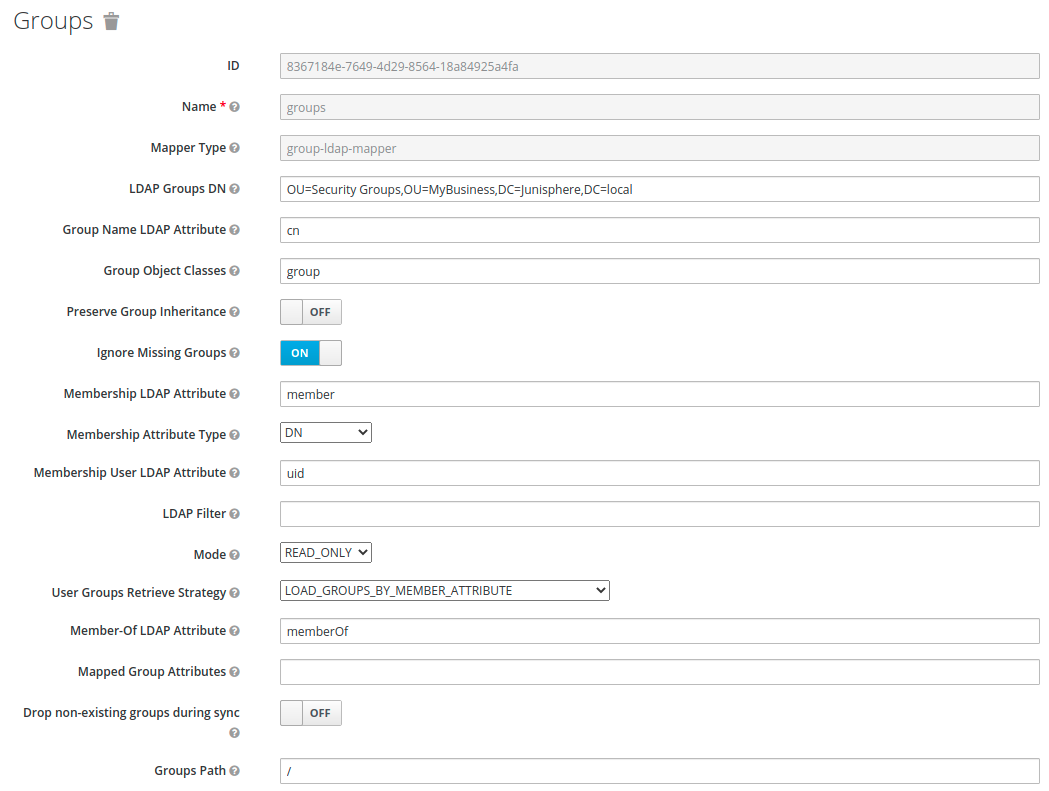
One very important step is to add a mapper of type group-ldap-mapper.
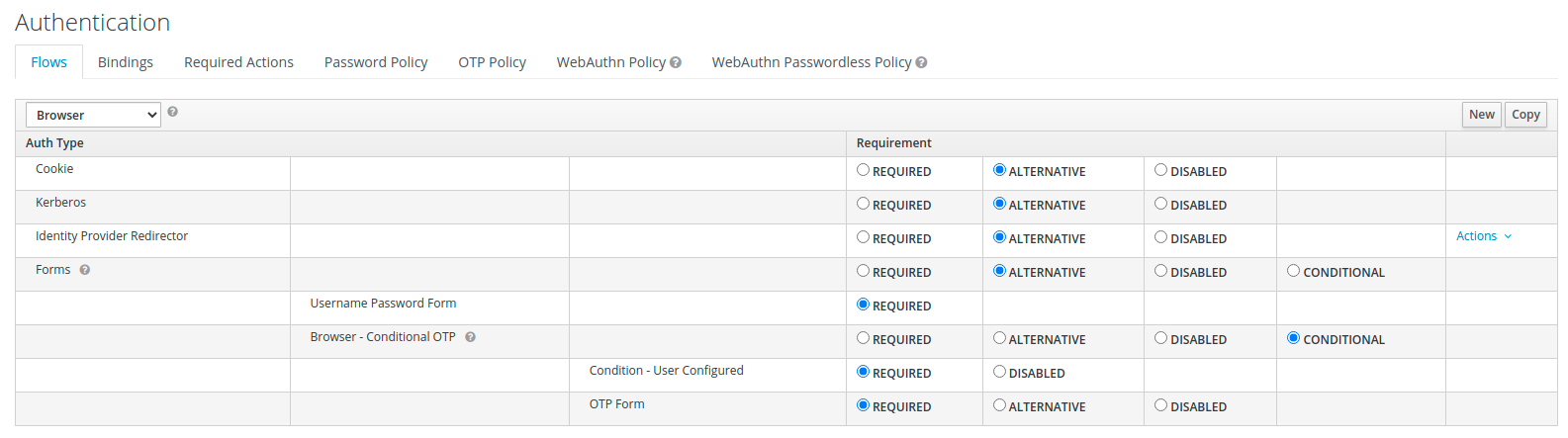
Kerberos
If Kerberos SSO is needed, this can be activated in the Authentication menu