User authentication types
Several methods of user authentication are available for logging into the SKOOR Engine web interface:
Local authentication
Authentication against an LDAP or Active Directory based on user name and password
Authentication against an LDAP or Active Directory based on a user's membership in a specific LDAP/Active Directory group
Login based on external authentication provider token (OIDC), such as Keycloak or Azure AD
Local authentication is always available. However, the other ones are only available if the respective configuration has been prepared on the system.
Locally authenticated user
The credentials for this type of user are stored in the local SKOOR Engine database. This is the default type of user. A password or valid email address must be set when a locally authenticated user is created.
The following user operations can only be performed by an administrator user:
Change user role
Change user type
Delete user
Change user’s group membership
A locally authenticated user can be linked to user groups that are associated with LDAP managed users but the user does not inherit any of the group's parameter settings.
Remote authenticated user
To authenticate a user against AD/LDAP, select the Remote authenticated parameter from its User type dropdown list. The user name must be identical to the one used in the AD/LDAP directory. Even though the user’s credentials will be checked against LDAP, an initial password must still be set when setting up a new Remote authenticated user. However, any password can be chosen.
Once the user is set up and a network connectivity to the AD/LDAP server is available from SKOOR Engine, login to SKOOR Engine’s web interface using the LDAP credentials. If login succeeds, the initially set password is overwritten with the valid LDAP password. The password is cached locally to allow login, should the connection to the LDAP server fail.
Changing an LDAP authenticated user’s password is not supported from within SKOOR Engine. The password must be changed in LDAP.
Existing locally authenticated users can be changed to LDAP authenticated
Existing LDAP authenticated userss can be changed to locally authenticated. The current LDAP password will be saved and used for local authentication
LDAP managed user
An LDAP managed user is not created manually within SKOOR Engine. It is auto-created once a user logs in who belongs to a specific group in the LDAP directory.
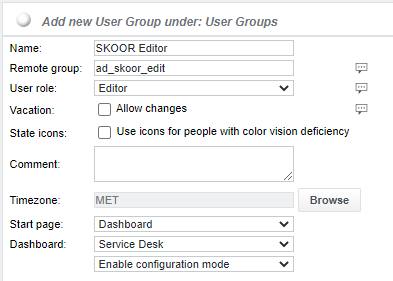
When a SKOOR Engine user group is created (see section User groups), the LDAP group name must be configured as Remote group in the Add new User Group dialog.
Once a Remote group name is entered, additional parameters can be configured for the group:
Set the reqiured User role for the LDAP group. Also, a start page can be chosen.
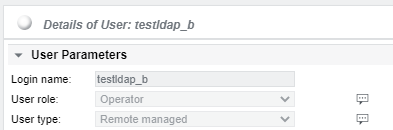
Once a user tries to login, an authentication is performed against the configured LDAP server. If the login succeeds and the user is a member of the configured LDAP group, the user is automatically created as an object under /root /Users /Users:
In this example, the user testldap_b was automatically created as User type Remote managed. The user cannot be edited. The full name, telephone number and email address are provided by the LDAP directory if the respective mappings are configured (see LDAP Authentication Setup ). The newly created user account is automatically added to the corresponding SKOOR LDAP user group.
If a user is member of multiple groups in the LDAP directory and those groups are also configured in SKOOR Engine, the user object is linked to all of these groups. It will inherit the highest privileges (e.g. User role Administrator) of the linked groups.
An LDAP managed user can not be linked to additional user groups.
An LDAP managed user can be deleted manually (by administrator users) or it is deleted automatically after a predefined number of days.
The LDAP group membership is determined using the memberOf attribute of the user. The attribute can be changed by editing the ldap_item_group entry in the eranger-server.cfg configuration file.